Global Mass Surveillance
- The Fourteen Eyes
The UKUSA Agreement is an agreement between the United Kingdom, United States, Australia, Canada, and New Zealand to cooperatively collect, analyze, and share intelligence. Members of this group, known as the Five Eyes, focus on gathering and analyzing intelligence from different parts of the world. While Five Eyes countries have agreed to not spy on each other as adversaries, leaks by Snowden have revealed that some Five Eyes members monitor each other's citizens and share intelligence to avoid breaking domestic laws that prohibit them from spying on their own citizens. The Five Eyes alliance also cooperates with groups of third-party countries to share intelligence (forming the Nine Eyes and Fourteen Eyes), however Five Eyes and third-party countries can and do spy on each other.
During the 2013 NSA leaks
Internet spying scandal, the surveillance agencies of the "Five Eyes"
have been accused of intentionally spying on one another's citizens and
willingly sharing the collected information with each other, allegedly
circumventing laws preventing each agency from spying on its own
citizens.
Internet spying scandal, the surveillance agencies of the "Five Eyes"
have been accused of intentionally spying on one another's citizens and
willingly sharing the collected information with each other, allegedly
circumventing laws preventing each agency from spying on its own
citizens.
The 2013 NSA leaks are not entirely new, but rather, they are a
confirmation of earlier disclosures about the UK-US espionage alliance.
For example, the British newspaper The Independent reported back in 1996 that the U.S. National Security Agency "taps UK phones" at the request of the British intelligence agency MI5, thus allowing British agents to evade restrictive limitations on domestic telephone tapping.
confirmation of earlier disclosures about the UK-US espionage alliance.
For example, the British newspaper The Independent reported back in 1996 that the U.S. National Security Agency "taps UK phones" at the request of the British intelligence agency MI5, thus allowing British agents to evade restrictive limitations on domestic telephone tapping.
The mutual surveillance and sharing of information between allies of the UK and US resurfaced again during the 2013 mass surveillance disclosures. As described by the news magazine Der Spiegel, this was done to circumvent domestic surveillance regulations:
Britain's GCHQ intelligence agency can spy on anyone but
British nationals, the NSA can conduct surveillance on anyone but
Americans, and Germany's BND (Bundesnachrichtendienst)
foreign intelligence agency can spy on anyone but Germans. That's how a
matrix is created of boundless surveillance in which each partner aids
in a division of roles.
They exchanged information. And they worked together extensively. That
applies to the British and the Americans, but also to the BND, which
assists the NSA in its Internet surveillance
According to The Guardian, the "Five Eyes" community is an exclusive club where new members "do not seem to be welcome":
It does not matter how senior you are, and how close a friend you think you are to Washington or London, your communications could easily be being shared among the handful of white, English-speaking nations with membership privileges.
In 2013, Canadian federal judge Richard Mosley strongly rebuked the Canadian Security Intelligence Service (CSIS)
for outsourcing its surveillance of Canadians to overseas partner
agencies. A 51-page ruling says that the CSIS and other Canadian federal
agencies are illegally enlisting U.S. and British allies in global surveillance dragnets, while keeping domestic federal courts in the dark.
for outsourcing its surveillance of Canadians to overseas partner
agencies. A 51-page ruling says that the CSIS and other Canadian federal
agencies are illegally enlisting U.S. and British allies in global surveillance dragnets, while keeping domestic federal courts in the dark.
Who is required to hand over the encryption keys to authorities?
Mandatory key disclosure laws require individuals to turn over encryption keys to law enforcement conducting a criminal investigation. How these laws are implemented (who may be legally compelled to assist) vary from nation to nation, but a warrant is generally required. Defenses against key disclosure laws include steganography and encrypting data in a way that provides plausible deniability.
Steganography involves hiding sensitive information (which may be encrypted) inside of ordinary data (for example, encrypting an image file and then hiding it in an audio file). With plausible deniability, data is encrypted in a way that prevents an adversary from being able to prove that the information they are after exists (for example, one password may decrypt benign data and another password, used on the same file, could decrypt sensitive data).
* (people who know how to access a system may be ordered to share their knowledge, however, this doesn't apply to the suspect itself or family members.)
Surveillance Self-Defense
Tips, Tools and How-tos for Safer Online Communications
VPN providers with extra layers of privacy
All providers listed here are outside the US, use encryption, accept Bitcoin, support OpenVPN and have a no logging policy.
 | Free | Yes | 325 | Switzerland | ProtonVPN.com |
 | Free | Yes | 160+ | Malaysia | hide.me |
 | $ 35.88 | No | 27 | Sweden | FrootVPN.com |
 | $ 39.99 | No | 128 | Hong Kong | VPN.ht |
 | $ 39.95 | Yes | 164 | Seychelles | Trust.Zone |
 | $ 40 | No | 300+ | Seychelles | Proxy.sh |
 | 35.88 € | No | 800+ | Seychelles | VPNTunnel.com |
 | 45 € | Yes | 22 | Sweden | AzireVPN.com |
 | $ 52 | Yes | 28 | Iceland | Cryptostorm.is |
 | 49 € | Yes | 31 | Hong Kong | blackVPN.com |
 | $ 59 | Yes | 204 | Bulgaria | VPNArea.com |
 | 54 € | Yes | 162 | Italy | AirVPN.org |
 | 60 € | Yes | 281 | Sweden | Mullvad.net |
 | $ 83.88 | Yes | 5200+ | Panama | NordVPN.com |
 | 84 € | Yes | 67 | Sweden | OVPN.com |
 | $ 100 | Yes | 38 | Gibraltar | IVPN.net |
 | $ 99.95 | Yes | 148 | British Virgin Islands | ExpressVPN.com |
 | 119.99 € | No | 54 | Switzerland | Perfect-Privacy.com |
Why is it not recommended to choose a US-based service?
Services based in the United States are not recommended because of the country's surveillance programs, use of National Security Letters
(NSLs) and accompanying gag orders, which forbid the recipient from
talking about the request. This combination allows the government to secretly force companies to grant complete access to customer data and transform the service into a tool of mass surveillance.
(NSLs) and accompanying gag orders, which forbid the recipient from
talking about the request. This combination allows the government to secretly force companies to grant complete access to customer data and transform the service into a tool of mass surveillance.
An example of this is Lavabit – a discontinued secure email service created by Ladar Levison. The FBI requested
Snowden's records after finding out that he used the service. Since
Lavabit did not keep logs and email content was stored encrypted, the
FBI served a subpoena (with a gag order) for the service's SSL keys.
Having the SSL keys would allow them to access
communications (both metadata and unencrypted content) in real time for
all of Lavabit's customers, not just Snowden's.
Snowden's records after finding out that he used the service. Since
Lavabit did not keep logs and email content was stored encrypted, the
FBI served a subpoena (with a gag order) for the service's SSL keys.
Having the SSL keys would allow them to access
communications (both metadata and unencrypted content) in real time for
all of Lavabit's customers, not just Snowden's.
Ultimately, Levison turned over the SSL keys and shut down the service at the same time. The US government then threatened Levison with arrest, saying that shutting down the service was a violation of the court order.
What is a warrant canary?
A warrant canary is a posted document stating that an organization has
not received any secret subpoenas during a specific period of time. If
this document fails to be updated during the specified time then the
user is to assume that the service has received such a subpoena and
should stop using the service.
not received any secret subpoenas during a specific period of time. If
this document fails to be updated during the specified time then the
user is to assume that the service has received such a subpoena and
should stop using the service.
click
here :: Parrot Security Professional tools for security testing,
software development and privacy defense, all in one place.
WikiLeaks-related Twitter court orders
 | |
Browser Recommendation
Browser Fingerprint - Is your browser configuration unique?
Your Browser sends information that makes you unique amongst millions of users and therefore easy to identify.
When you visit a web page, your browser voluntarily sends information
about its configuration, such as available fonts, browser type, and
add-ons. If this combination of information is unique, it may be
possible to identify and track you without using cookies.
about its configuration, such as available fonts, browser type, and
add-ons. If this combination of information is unique, it may be
possible to identify and track you without using cookies.
You need to find what most browsers are reporting,
and then use those variables to bring your browser in the same
population. This means having the same fonts, plugins, and extensions
installed as the large installed base. You should have a spoofed user agent string
to match what the large userbase has. You need to have the same
settings enabled and disabled, such as DNT and WebGL. You need your
browser to look as common as everyone else. Disabling JavaScript, using
Linux, or even the TBB, will make your browser stick out from the
masses.
and then use those variables to bring your browser in the same
population. This means having the same fonts, plugins, and extensions
installed as the large installed base. You should have a spoofed user agent string
to match what the large userbase has. You need to have the same
settings enabled and disabled, such as DNT and WebGL. You need your
browser to look as common as everyone else. Disabling JavaScript, using
Linux, or even the TBB, will make your browser stick out from the
masses.
Modern web browsers have not been architected to assure personal web
privacy. Rather than worrying about being fingerprinted, it seems more
practical to use free software plugins
like Privacy Badger, uBlock Origin and Disconnect. They not only
respect your freedom, but your privacy also. You can get much further
with these than trying to manipulate your browser's fingerprint.
privacy. Rather than worrying about being fingerprinted, it seems more
practical to use free software plugins
like Privacy Badger, uBlock Origin and Disconnect. They not only
respect your freedom, but your privacy also. You can get much further
with these than trying to manipulate your browser's fingerprint.
DEF CON 25 - Roger Dingledine - Next Generation Tor Onion Services
WebRTC IP Leak Test - Is your IP address leaking?
WebRTC is a new communication protocol that relies on JavaScript that can leak your actual IP address from behind your VPN.
While software like NoScript prevents this, it's probably a good idea to block this protocol directly as well, just to be safe.
test browser now
How to disable WebRTC in Firefox?
In short: Set "media.peerconnection.enabled" to "false" in "about:config".
Explained:
- Enter "about:config" in the firefox address bar and press enter.
- Press the button "I'll be careful, I promise!"
- Search for "media.peerconnection.enabled"
- Double click the entry, the column "Value" should now be "false"
- Done. Do the WebRTC leak test again.
If you want to make sure every single WebRTC related setting is really disabled change these settings:
- media.peerconnection.turn.disable = true
- media.peerconnection.use_document_iceservers = false
- media.peerconnection.video.enabled = false
- media.peerconnection.identity.timeout = 1
Now you can be 100% sure WebRTC is disabled.
test browser again
Firefox Privacy Add-ons

Stop Tracking with Privacy Badger
Privacy Badger is a browser add-on that stops
advertisers and other third-party trackers from secretly tracking where
you go and what pages you look at on the web. Privacy Badger learns
about trackers as you browse by inspecting external resources websites
request. Please be aware that Google Analytics is considered first-party
by Privacy Badger, which means that Google Analytics will not be
blocked if you do not use another blocker, such as uBlock Origin.
advertisers and other third-party trackers from secretly tracking where
you go and what pages you look at on the web. Privacy Badger learns
about trackers as you browse by inspecting external resources websites
request. Please be aware that Google Analytics is considered first-party
by Privacy Badger, which means that Google Analytics will not be
blocked if you do not use another blocker, such as uBlock Origin.

Block Ads and Trackers with uBlock Origin
An efficient wide-spectrum-blocker
that's easy on memory, and yet can load and enforce thousands more
filters than other popular blockers out there. It has no monetization
strategy and is completely open source.
We recommend Firefox but uBlock Origin also works in other browsers
such as Safari, Opera, and Chromium. Unlike AdBlock Plus, uBlock does
not allow so-called "acceptable ads".
that's easy on memory, and yet can load and enforce thousands more
filters than other popular blockers out there. It has no monetization
strategy and is completely open source.
We recommend Firefox but uBlock Origin also works in other browsers
such as Safari, Opera, and Chromium. Unlike AdBlock Plus, uBlock does
not allow so-called "acceptable ads".

Automatically Delete Cookies with Cookie AutoDelete
Automatically removes cookies when they are no longer used by open
browser tabs. With the cookies, lingering sessions, as well as
information used to spy on you, will be expunged.
browser tabs. With the cookies, lingering sessions, as well as
information used to spy on you, will be expunged.

Encryption with HTTPS Everywhere
A Firefox, Chrome, and Opera extension that encrypts your
communications with many major websites, making your browsing more
secure. A collaboration between The Tor Project and the Electronic
Frontier Foundation.
communications with many major websites, making your browsing more
secure. A collaboration between The Tor Project and the Electronic
Frontier Foundation.

Block Content Delivery Networks with Decentraleyes
Emulates Content Delivery Networks locally by intercepting requests,
finding the required resource and injecting it into the environment.
This all happens instantaneously, automatically, and no prior
configuration is required.
Source code: GitLab (self-hosted).finding the required resource and injecting it into the environment.
This all happens instantaneously, automatically, and no prior
configuration is required.
The following add-ons require quite a lot of interaction from
the user to get things working. Some sites will not work properly until
you have configured the add-ons.
Stop cross-site requests with uMatrix
Many websites integrate features which let other websites track you,
such as Facebook Like Buttons or Google Analytics. uMatrix gives you
control over the requests that websites make to other websites. This
gives you greater and more fine-grained control over the information
that you leak online.
such as Facebook Like Buttons or Google Analytics. uMatrix gives you
control over the requests that websites make to other websites. This
gives you greater and more fine-grained control over the information
that you leak online.
Be in total control with NoScript Security Suite
Highly customizable plugin to selectively allow JavaScript, Java,
and Flash to run only on websites you trust. Not for casual users, it
requires technical knowledge to configure.
and Flash to run only on websites you trust. Not for casual users, it
requires technical knowledge to configure.
How the Feds Caught Russian Mega-Carder Roman Seleznev
Firefox: Privacy Related "about:config" Tweaks
Preparation:
- Enter "about:config" in the firefox address bar and press enter.
- Press the button "I'll be careful, I promise!"
- Follow the instructions below...
Getting started:
- privacy.firstparty.isolate = true
A result of the Tor Uplift effort, this preference isolates all browser identifier sources (e.g. cookies) to the first party domain, with the goal of preventing tracking across different domains. (Don't do this if you are using the Firefox Addon "Cookie AutoDelete" with Firefox v58 or below.)
privacy.resistFingerprinting = true
A result of the Tor Uplift effort, this preference makes Firefox more resistant to browser fingerprinting.
privacy.trackingprotection.enabled = true
This is Mozilla's new built-in tracking protection. It uses Disconnect.me filter list, which is redundant if you are already using uBlock Origin 3rd party filters, therefore you should set it to false if you are using the add-on functionalities.
browser.cache.offline.enable = false
Disables offline cache.
browser.safebrowsing.malware.enabled = false
Disable Google Safe Browsing malware checks. Security risk, but privacy improvement.
browser.safebrowsing.phishing.enabled = false
Disable Google Safe Browsing and phishing protection. Security risk, but privacy improvement.
browser.send_pings = false
The attribute would be useful for letting websites track visitors' clicks.
browser.sessionstore.max_tabs_undo = 0
Even with Firefox set to not remember history, your closed tabs are stored temporarily at Menu -> History -> Recently Closed Tabs.
browser.urlbar.speculativeConnect.enabled = false
Disable preloading of autocomplete URLs. Firefox preloads URLs that autocomplete when a user types into the address bar, which is a concern if URLs are suggested that the user does not want to connect to.
dom.battery.enabled = false
Website owners can track the battery status of your device.
dom.event.clipboardevents.enabled = false
Disable that websites can get notifications if you copy, paste, or cut something from a web page, and it lets them know which part of the page had been selected.
geo.enabled = false
Disables geolocation.
media.eme.enabled = false
Disables playback of DRM-controlled HTML5 content, which, if enabled, automatically downloads the Widevine Content Decryption Module provided by Google Inc. Details
DRM-controlled content that requires the Adobe Flash or Microsoft Silverlight NPAPI plugins will still play, if installed and enabled in Firefox.
media.gmp-widevinecdm.enabled = false
Disables the Widevine Content Decryption Module provided by Google Inc., used for the playback of DRM-controlled HTML5 content.
media.navigator.enabled = false
Websites can track the microphone and camera status of your device.
network.cookie.cookieBehavior = 1
Disable cookies
0 = Accept all cookies by default
1 = Only accept from the originating site (block third-party cookies)
2 = Block all cookies by default
network.cookie.lifetimePolicy = 2
cookies are deleted at the end of the session
0 = Accept cookies normally
1 = Prompt for each cookie
2 = Accept for current session only
3 = Accept for N days
network.http.referer.trimmingPolicy = 2
Send only the scheme, host, and port in the Referer header
0 = Send the full URL in the Referer header
1 = Send the URL without its query string in the Referer header
2 = Send only the scheme, host, and port in the Referer header
network.http.referer.XOriginPolicy = 2
Only send Referer header when the full hostnames match. (Note: if you notice significant breakage, you might try 1 combined with an XOriginTrimmingPolicy tweak below.)
0 = Send Referer in all cases
1 = Send Referer to same eTLD sites
2 = Send Referer only when the full hostnames match
network.http.referer.XOriginTrimmingPolicy = 2
When sending Referer across origins, only send scheme, host, and port in the Referer header of cross-origin requests.
0 = Send full url in Referer
1 = Send url without query string in Referer
2 = Only send scheme, host, and port in Referer
webgl.disabled = true
WebGL is a potential security risk.
browser.sessionstore.privacy_level = 2
This preference controls when to store extra information about a session: contents of forms, scrollbar positions, cookies, and POST data.
0 = Store extra session data for any site. (Default starting with Firefox 4.)
1 = Store extra session data for unencrypted (non-HTTPS) sites only. (Default before Firefox 4.)
2 = Never store extra session data
network.IDN_show_punycode = true
Not rendering IDNs as their Punycode equivalent leaves you open to phishing attacks that can be very difficult to notice.
extensions.blocklist.url = https://blocklists.settings.services.mozilla.com/v1/blocklist/3/%20/%20/
Limit the amount of identifiable information sent when requesting the Mozilla harmful extension blocklist.
Optionally, the blocklist can be disabled entirely by setting extensions.blocklist.enabled to false for increased privacy, but decreased security.
Related Information
- ffprofile.com - Helps you to create a Firefox profile with the defaults you like.
- mozillazine.org - Security and privacy-related preferences.
- user.js Firefox hardening stuff
- This is a user.js configuration file for Mozilla Firefox that's
supposed to harden Firefox's settings and make it more secure. - Privacy Settings - A Firefox add-on to alter built-in privacy settings easily with a toolbar panel.
Privacy-Conscious Email Providers - No Affiliates
Interesting Email Providers Under Development
Become Your Own Email Provider with Mail-in-a-Box Take it a step further and get control of your email with this easy-to-deploy mail server in a box. Mail-in-a-Box lets you become your own mail service provider in a few easy steps. It's sort of like making your own Gmail, but one you control from top to bottom. Technically, Mail-in-a-Box turns a fresh cloud computer into a working mail server. But you don't need to be a technology expert to set it up. More: https://mailinabox.email/ Privacy Email Tools
Related Information
Email ClientsThunderbird Mozilla MozillaThunderbird is a free, open source, cross-platform email, news, and chat client developed by the Mozilla Foundation. Thunderbird is an email, newsgroup, news feed, and chat (XMPP, IRC, Twitter) client. OS: Windows, macOS, Linux, BSD. Claws Mail Claws ClawsMail is a free and open source, GTK+-based email and news client. It offers easy configuration and an abundance of features. It is included with Gpg4win, an encryption suite for Windows. OS: Windows, macOS, Linux, BSD, Solaris, Unix. Worth Mentioning
Email AlternativesBitmessage Bitmessage Bitmessageis a P2P communications protocol used to send encrypted messages to another person or to many subscribers. It is decentralized and trustless, meaning that you need-not inherently trust any entities like root certificate authorities. It uses strong authentication which means that the sender of a message cannot be spoofed, and it aims to hide "non-content" data. OS: Windows, macOS, Linux. RetroShare Retroshare Retrosharecreates encrypted connections to your friends. Nobody can spy on you. Retroshare is completely decentralized. This means there are no central servers. It is entirely Open-Source and free. There are no costs, no ads and no Terms of Service. OS: Windows, macOS, Linux. Worth Mentioning
DEF CON 22 - Zoz - Don't Fuck It Up!Privacy Respecting Search Engines If you are currently using search engines like Google, Bing or Yahoo, you should pick an alternative here. searx An open source An open sourcemetasearch engine, aggregating the results of other search engines while not storing information about its users. No logs, no ads and no tracking. StartPage Google Googlesearch results, with complete privacy protection. Behind StartPage is a European company that has been obsessive about privacy since 2006. DuckDuckGo The search engine that doesn't track you. Some of DuckDuckGo's code is free software hosted at GitHub, but the core is proprietary. The company is based in the USA. The search engine that doesn't track you. Some of DuckDuckGo's code is free software hosted at GitHub, but the core is proprietary. The company is based in the USA.Firefox Addon
Worth Mentioning
Encrypted Instant MessengerIf you are currently using an Instant Messenger like WhatsApp, Viber, LINE, Telegram or Threema, you should pick an alternative here. Mobile: Signal Signal Signalis a mobile app developed by Open Whisper Systems. The app provides instant messaging, as well as voice and video calling. All communications are end-to-end encrypted. Signal is free and open source, enabling anyone to verify its security by auditing the code. The development team is supported by community donations and grants. There are no advertisements, and it doesn't cost anything to use. OS: Android, iOS, macOS, Windows, Linux Riot.imbeta  Riot.im is a decentralized free-software chatting application based on the Matrix Riot.im is a decentralized free-software chatting application based on the Matrixprotocol, a recent open protocol for real-time communication offering E2E encryption. It can bridge other communications via others protocols such as IRC too. OS: Android, iOS, macOS, Windows, Linux, Web Desktop: Ricochet Ricochet uses the Tor network to reach your contacts without relying on messaging servers. It creates a hidden service, which is used to rendezvous with Ricochet uses the Tor network to reach your contacts without relying on messaging servers. It creates a hidden service, which is used to rendezvous withyour contacts without revealing your location or IP address. Instead of a username, you get a unique address that looks like ricochet:rs7ce36jsj24ogfw. Other Ricochet users can use this address to send a contact request - asking to be added to your contacts list. OS: Windows, macOS, Linux. Worth Mentioning
Related Information
Encrypted Video & Voice MessengerIf you are currently using a Video & Voice Messenger like Skype, Viber or Google Hangouts, you should pick an alternative here. Mobile: Signal Signal is a mobile app developed by Open Whisper Systems. The app provides instant messaging, as well as voice and video calling. All communications are end-to-end encrypted. Signal is free and open source, enabling anyone to verify its security by auditing the code. The development team is supported by community donations and grants. There are no advertisements, and it doesn't cost anything to use. OS: Android, iOS, macOS, Windows, Linux Wire Wire Wireis an app developed by Wire Swiss GmbH. The Wire app allows users to exchange end-to-end encrypted instant messages, as well as make voice and video calls. Wire is free and open source, enabling anyone to verify its security by auditing the code. The development team is backed by Iconical and they will monetize in the future with premium features/services. Caution: The company keeps a list of all the users you contact until you delete your account. OS: Android, iOS, macOS, Windows, Linux, Web Linphone Linphone is an open source SIP Phone and a free voice over IP service, available on mobile and desktop environments and on web browsers. It supports ZRTP for end-to-end encrypted voice and video communication. OS: iOS, Android, Windows Phone, Linux, Windows, macOS, Browser (Web) Worth Mentioning
File SharingOnionShare OnionShare OnionShareis an open source tool that lets you securely and anonymously share a file of any size. It works by starting a web server, making it accessible as a Tor onion service, and generating an unguessable URL to access and download the files. It doesn't require setting up a server on the internet somewhere or using a third-party filesharing service. You host the file on your own computer and use a Tor onion service to make it temporarily accessible over the internet. Magic Wormhole Get things from one computer to another, safely. This package provides a library and a command-line tool named wormhole, which makes it possible to get arbitrary-sized files and directories (or short pieces of text) from one computer to another. The two endpoints are identified by using identical "wormhole codes": in general, the sending machine generates and displays the code, which must then be typed into the receiving machine. The codes are short and human-pronounceable, using a phonetically-distinct wordlist. The receiving side offers tab-completion on the codewords, so usually only a few characters must be typed. Wormhole codes are single-use and do not need to be memorized. OS: cross-platform (python) Encrypted Cloud Storage ServicesIf you are currently using Cloud Storage Services like Dropbox, Google Drive, Microsoft OneDrive or Apple iCloud, you should pick an alternative here. Nextcloud - Choose your hoster Similar Similarfunctionally to the widely used Dropbox, with the difference being that Nextcloud is free and open-source, and thereby allowing anyone to install and operate it without charge on a private server, with no limits on storage space or the number of connected clients. Client OS: Windows, macOS, Linux, BSD, Unix, iOS, Android, Fire OS. Server: Linux. Least Authority S4 - For Experts S4 S4(Simple Secure Storage Service) is Least Authority's verifiably secure off-site backup system for individuals and businesses. 100% client-side encryption and open source transparency. 250GB for $9.95/month or 5TB for $25.95/month. Servers are hosted with Amazon S3 in the US. OS: Linux, Windows, macOS, OpenSolaris, BSD. (Installation for advanced users) Worth Mentioning
Self-Hosted Cloud Server SoftwareIf you are currently using a Cloud Storage Services like Dropbox, Google Drive, Microsoft OneDrive or Apple iCloud, you should think about hosting it on your own. Pydio Pydio Pydiois open source software that turns instantly any server (on-premise, NAS, cloud IaaS or PaaS) into a file sharing platform for your company. It is an alternative to SaaS Boxes and Drives, with more control, safety and privacy, and favorable TCOs. OS: Windows, macOS, Linux, iOS, Android. Tahoe-LAFS Tahoe-LAFS Tahoe-LAFSis a Free and Open decentralized cloud storage system. It distributes your data across multiple servers. Even if some of the servers fail or are taken over by an attacker, the entire file store continues to function correctly, preserving your privacy and security. OS: Windows, macOS, Linux. Nextcloud Similar Similarfunctionally to the widely used Dropbox, with the difference being that Nextcloud is free and open-source, and thereby allowing anyone to install and operate it without charge on a private server, with no limits on storage space or the number of connected clients. Client OS: Windows, macOS, Linux, BSD, Unix, iOS, Android, Fire OS. Server: Linux. Worth Mentioning
Secure Hosting ProviderBAHNHOF BAHNHOF is a widely known 'bullet-proof' hosting company Colocation: DataCell DataCell is a data center providing secure colocating in Switzerland and Iceland. VPS/Web Hosting: Orange Website Orange Website is an Icelandic web hosting provider that prides themselves in protecting online privacy and free speech. Secure File Sync SoftwareSparkleShare SparkleShare creates a special folder on your computer. You can add remotely hosted folders (or "projects") to this folder. These projects will be automatically kept in sync with both the host and all of your peers when someone adds, removes or edits a file. OS: Windows, macOS, Linux. Syncthing Syncthing replaces proprietary sync and cloud services with something open, trustworthy and decentralized. Your data is your data alone and you deserve to choose where it is stored, if it is shared with some third-party and how it's transmitted over the Internet. OS: Windows, macOS, Linux, Android, BSD, Solaris. Worth Mentioning
Password Manager SoftwareIf you are currently using a password manager software like 1Password, LastPass, Roboform or iCloud Keychain, you should use an alternative Bitwarden - Cloud/Self-host Bitwarden Bitwardenis a free and open source password manager. It aims to solve password management problems for individuals, teams, and business organizations. Bitwarden is among the easiest and safest solutions to store all of your logins and passwords while conveniently keeping them synced between all of your devices. If you don't want to use the Bitwarden cloud, you can easily host your own Bitwarden server. OS: Windows, macOS, Linux, iOS, Android, Web. KeePass / KeePassXC - Local KeePass KeePassis a free open source password manager, which helps you to manage your passwords in a secure way. All passwords in one database, which is locked with one master key or a key file. The databases are encrypted using the best and most secure encryption algorithms currently known: AES and Twofish. See also: KeePassXC with official native cross-platform support for Windows/macOS/Linux. OS: Windows, macOS, Linux, iOS, Android, BSD. LessPass - Browser LessPass LessPassis a free and open source password manager that generates unique passwords for websites, email accounts, or anything else based on a master password and information you know. No sync needed. Uses PBKDF2 and SHA-256. It's advised to use the browser addons for more security. OS: Windows, macOS, Linux, Android. Worth Mentioning
Calendar and Contacts SyncIf you are currently using a calendar and or contacts synchronization service like Google Sync or iCloud, you should pick an alternative here. Nextcloud NextCloud NextCloudis a suite of client-server software for creating and using file hosting services. This includes calendar sync via CalDAV and contacts sync via CardDAV. Nextcloud is free and open-source, thereby allowing anyone to install and operate it without charge on a private server. Client OS: Windows, macOS, Linux, BSD, Unix, iOS, Android, Fire OS. Server: Linux. Email Providers Many email providers also offer calendar and or contacts sync services. Refer to the Email Providers section to choose an email provider and check if they also offer calendar and or contacts sync. Many email providers also offer calendar and or contacts sync services. Refer to the Email Providers section to choose an email provider and check if they also offer calendar and or contacts sync.OS: depends on email provider. EteSync EteSync EteSyncis a secure, end-to-end encrypted and journaled personal information (e.g. contacts and calendar) cloud synchronization and backup for Android and any OS that supports CalDAV/CardDAV. It costs $14 per year to use, or you can host the server yourself for free. Client OS: Android, Web. Server OS: Linux. Worth Mentioning
File Encryption SoftwareIf you are currently not using encryption software for your hard disk, emails or file archives, you should pick an encryption software here. VeraCrypt - Disk Encryption VeraCrypt VeraCryptis a source-available freeware utility used for on-the-fly encryption. It can create a virtual encrypted disk within a file or encrypt a partition or the entire storage device with pre-boot authentication. VeraCrypt is a fork of the discontinued TrueCrypt project. It was initially released on June 22, 2013. According to its developers, security improvements have been implemented and issues raised by the initial TrueCrypt code audit have been addressed. OS: Windows, macOS, Linux. GNU Privacy Guard - Email Encryption GnuPG GnuPGis a GPL Licensed alternative to the PGP suite of cryptographic software. GnuPG is compliant with RFC 4880, which is the current IETF standards track specification of OpenPGP. Current versions of PGP (and Veridis' Filecrypt) are interoperable with GnuPG and other OpenPGP-compliant systems. GnuPG is a part of the Free Software Foundation's GNU software project, and has received major funding from the German government. GPGTools for macOS. OS: Windows, macOS, Linux, Android, BSD. PeaZip - File Archive Encryption PeaZip PeaZipis a free and open-source file manager and file archiver made by Giorgio Tani. It supports its native PEA archive format (featuring compression, multi volume split and flexible authenticated encryption and integrity check schemes) and other mainstream formats, with special focus on handling open formats. It supports 181 file extensions (as of version 5.5.1). macOS alternative: Keka is a free file archiver. OS: Windows, Linux, BSD. Worth Mentioning
Self-contained NetworksTor Browser The TheTor network is a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet. Tor's users employ this network by connecting through a series of virtual tunnels rather than making a direct connection, thus allowing both organizations and individuals to share information over public networks without compromising their privacy. Tor is an effective censorship circumvention tool. I2P Anonymous Network The TheInvisible Internet Project (I2P) is a computer network layer that allows applications to send messages to each other pseudonymously and securely. Uses include anonymous Web surfing, chatting, blogging and file transfers. The software that implements this layer is called an I2P router and a computer running I2P is called an I2P node. The software is free and open source and is published under multiple licenses. OS: Windows, macOS, Linux, Android, BSD / Solaris. The Freenet Project Freenet Freenetis a peer-to-peer platform for censorship-resistant communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship. Both Freenet and some of its associated tools were originally designed by Ian Clarke, who defined Freenet's goal as providing freedom of speech on the Internet with strong anonymity protection. OS: Windows, macOS, Linux. Worth Mentioning
Decentralized Social Networks If you are currently using Social Networks like Facebook, Twitter or Google+, you should pick an alternative here. Mastodon Mastodon Mastodonis a social network based on open web protocols and free, open-source software. It is decentralized like e-mail. It also has the most users, and the most diverse (in terms of interests) users, looks good, and is easy to setup. diaspora* diaspora* diaspora*is based on three key philosophies: Decentralization, freedom and privacy. It is intended to address privacy concerns related to centralized social networks by allowing users set up their own server (or "pod") to host content; pods can then interact to share status updates, photographs, and other social data. Friendica Friendica Friendicahas an emphasis on extensive privacy settings and easy server installation. It aims to federate with as many other social networks as possible. Currently, Friendica users can integrate contacts from Facebook, Twitter, Diaspora, GNU social, App.net, Pump.io and other services in their social streams. Worth Mentioning
Related Information
Domain Name System (DNS)Njalla - Domain Registration Njalla Njallaonly needs your email or jabber address in order to register a domain name for you. Created by people from The Pirate Bay and IPredator VPN. Accepted Payments: Bitcoin, Litecoin, Monero, DASH, Bitcoin Cash and PayPal. A privacy-aware domain registration service. DNSCrypt - Tool A Aprotocol for securing communications between a client and a DNS resolver. The DNSCrypt protocol uses high-speed high-security elliptic-curve cryptography and is very similar to DNSCurve, but focuses on securing communications between a client and its first-level resolver. OpenNIC - Service OpenNIC OpenNICis an alternate network information center/alternative DNS root which lists itself as an alternative to ICANN and its registries. Like all alternative root DNS systems, OpenNIC-hosted domains are unreachable to the vast majority of the Internet. Only specific configuration in one's DNS resolver makes these reachable, and very few Internet service providers have this configuration. Worth Mentioning
Digital NotebookIf you are currently using an application like Evernote, Google Keep or Microsoft OneNote you should pick an alternative here. Standard Notes Standard StandardNotes is a simple and private notes app that makes your notes easy and available everywhere you are. Features end-to-end encryption on every platform, and a powerful desktop experience with themes and custom editors. OS: Windows, macOS, Linux, iOS, Android, Web. Turtl Turtl Turtllets you take notes, bookmark websites, and store documents for sensitive projects. From sharing passwords with your coworkers to tracking research on an article you're writing, Turtl keeps it all safe from everyone but you and those you share with. OS: Windows, macOS, Linux, Android. Worth Mentioning
Paste ServicesPrivateBin PrivateBin PrivateBinis a minimalist, open source online pastebin where the server has zero knowledge of pasted data. Data is encrypted/decrypted in the browser using 256bit AES. It is the improved version of ZeroBin. Zerobin.net Zerobin Zerobinis a minimalist, open source online pastebin where the server has zero knowledge of pasted data. Data is encrypted/decrypted in the browser using 256bit AES. Ghostbin Ghostbin Ghostbinsupports encryption, expiration, sessions, grant users to edit your notes and pastes up to one megabyte. You can also create your own account to keep track of your pastes. The software is good but ghostbin.com's security is worrisome. Worth Mentioning
Productivity ToolsCryptPad CryptPad CryptPadis a private-by-design alternative to popular office tools and cloud services. All content is end-to-end encrypted. It is free and open source, enabling anyone to verify its security by auditing the code. The development team is supported by donations and grants. No registration is required, and it can be used anonymously via Tor browser. OS: Linux, macOS, Windows, Web. Etherpad Etherpad Etherpadis a highly customizable Open Source online editor providing collaborative editing in really real-time. Etherpad allows you to edit documents collaboratively in real-time, much like a live multi-player editor that runs in your browser. Write articles, press releases, to-do lists, etc. OS: Windows, macOS, Linux. Write.as Write.as Write.asis a cross-platform, privacy-oriented blogging platform. It's anonymous by default, letting you publish without signing up. If you create an account, it doesn't require any personal information. No ads, distraction-free, and built on a sustainable business model. Worth Mentioning
PC Operating SystemsIf you are currently using a operating system like Microsoft Windows or Apple macOS, you should pick an alternative here. Qubes OS Qubes Qubesis an open-source operating system designed to provide strong security for desktop computing. Qubes is based on Xen, the X Window System, and Linux, and can run most Linux applications and utilize most of the Linux drivers. Debian Debian Debianis a Unix-like computer operating system and a Linux distribution that is composed entirely of free and open-source software, most of which is under the GNU General Public License, and packaged by a group of individuals known as the Debian project. Trisquel Trisquel Trisquelis a Linux-based operating system derived from Ubuntu. The project aims for a fully free software system without proprietary software or firmware and uses Linux-libre, a version of the Linux kernel with the non-free code (binary blobs) removed. WarningWorth Mentioning
Live CD Operating SystemsTails Tails Tailsis a live operating system, that starts on almost any computer from a DVD, USB stick, or SD card. It aims at preserving privacy and anonymity, and helps to: Use the Internet anonymously and circumvent censorship; Internet connections go through the Tor network; leave no trace on the computer; use state-of-the-art cryptographic tools to encrypt files, emails and instant messaging. KNOPPIX Knoppix Knoppixis an operating system based on Debian designed to be run directly from a CD / DVD (Live CD) or a USB flash drive (Live USB), one of the first of its kind for any operating system. When starting a program, it is loaded from the removable medium and decompressed into a RAM drive. The decompression is transparent and on-the-fly. Puppy Linux Puppy PuppyLinux operating system is a lightweight Linux distribution that focuses on ease of use and minimal memory footprint. The entire system can be run from RAM with current versions generally taking up about 210 MB, allowing the boot medium to be removed after the operating system has started. Worth Mentioning
Mobile Operating SystemsEven though the source code of the following OS is provided, installing Google Apps may compromise your setup. The MicroG project can serve as a FLOSS replacement, depending on your threat model. LineageOS LineageOS LineageOSis a free and open-source operating system for smartphones and tablets, based on the official releases of Android by Google. It is the continuation of the CyanogenMod project. Worth Mentioning
Android Privacy Add-onsImprove your privacy with these add-ons for Android.  Control your traffic with NetGuardNetGuard provides simple and advanced ways to blockcertain apps' access to the internet without the help of root privileges. Applications and addresses can individually be allowed or denied access to your Wi-Fi and/or mobile connection, allowing you to control which apps are able to call home or not. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Welcome To The Oven (The End Of Censorship) | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| https://github.com/sbilly/awesome-security Surveillance Self-Defense https://canyouseeme.org/ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| https://nsa.gov1.info/surveillance/ https://archive.is/wip/75whA | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Surveillance Techniques: How Your Data Becomes Our DataIn 2001, NSA published the secret "Transition 2001" report defining our strategy for the 21st century. No longer could we simply access analog communications using conventional means, the new digital world of globally-networked encrypted communications required a dramatic change to our surveillance strategy: NSA would need to "live on the network". We've turned our nation's Internet and telecommunications companies into collection partners by installing filters in their facilities, serving them with secret court orders, building back doors into their software and acquiring keys to break their encryption. Backdoor SearchesSection 702 of the Foreign Intelligence Surveillance Act (FISA) provides us with a bonanza of "incidental" data collected from ordinary Americans communicating with foreigners targeted by this sweeping law. This convenient loophole allows us to peruse this database in our never-ending search for the elusive "needle in a haystack".Our Domestic Intercept StationsNSA technicians have installed intercept stations at key junction points, or switches, throughout the country. These switches are located in large windowless buildings owned by the major telecommunication companies and control the domestic internet traffic flow across the nation. A fiber optic splitter is placed on the incoming communication lines and routes the traffic to an NSA intercept station for processing.View a sample route that internet data traverses from a home in Toronto to the San Francisco Art Institute passing through several NSA intercept stations. 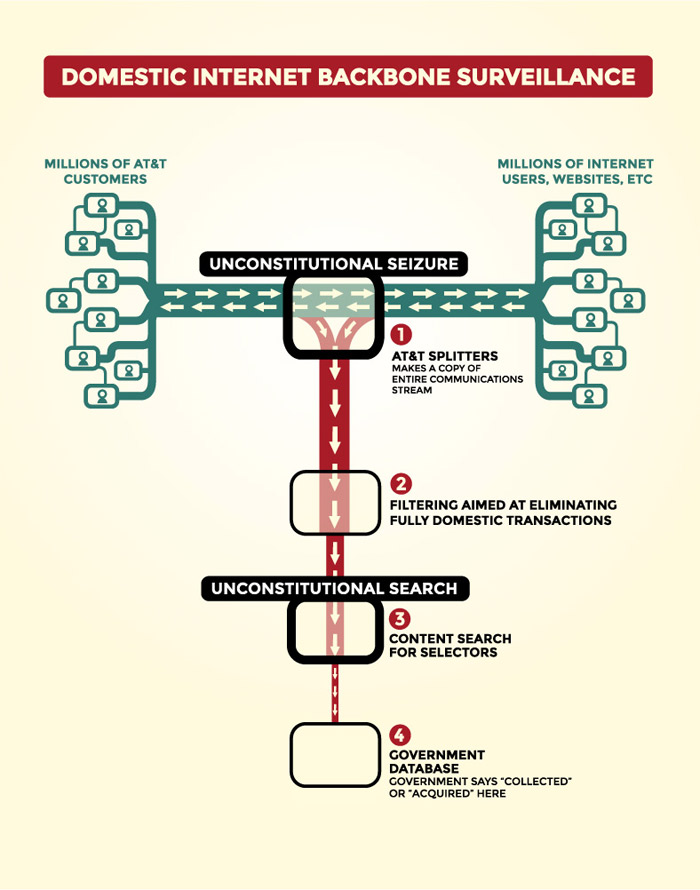 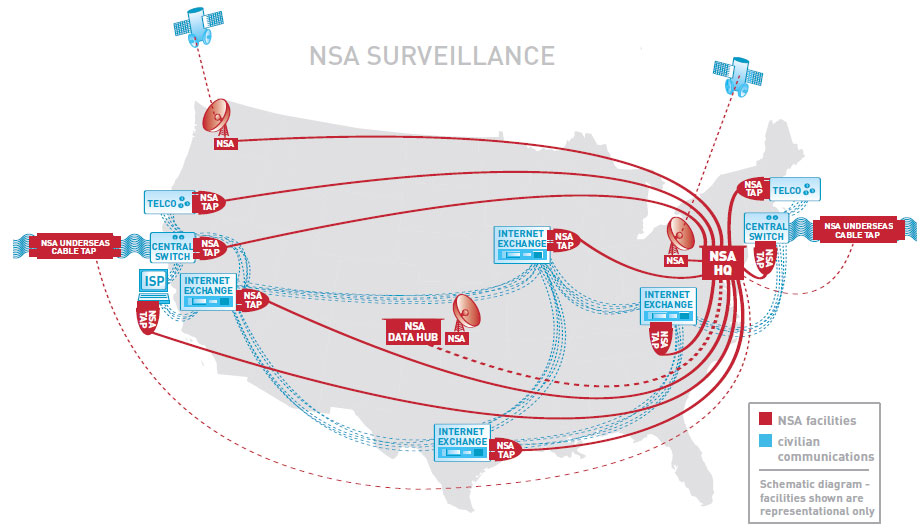 Larger version of map More information about this map Bulk Collection of U.S. Citizens' Phone RecordsIn the past, we used our close partnership with the FBI to collect bulk telephone records on an ongoing basis using a Top Secret order from the Foreign Intelligence Surveillance Court (FISC). The metadata we collected from this program gave us information about what communications you sent and received, who you talked to, where you were when you talked to them, the lengths of your conversations, and what kind of device you were using.In mid-2015, Congress passed the USA Freedom Act sadly ending this valuable bulk collection program for the time being. The PRISM Program: Our #1 Source of Raw IntelligenceOur partners at the FBI DITU (Data Intercept Technology Unit) extract information from the servers of nine major American internet companies: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple. This important partnership gives us direct access to audio, video, photographs, e-mails, documents and connection logs for each of these systems.Established in 2007, the Top Secret PRISM program has allowed us to closely track targeted individuals over time. Our ability to conduct live surveillance of search terms has given us important insights into their thoughts and intentions.  This slide lists our information providers and the type of data available to our analysts  This slide illustrates how the collected PRISM data flows through multiple NSA systems and databases To learn more about the PRISM program, view additional PRISM slides. Google Cloud ExploitationThe NSA "MUSCULAR" program allows us to conveniently conduct large-scale data gathering outside the jurisdiction of the Foreign Intelligence Surveillance Court by secretly tapping into the communication links between Google's data centers outside the U.S. The Special Source Operations (SSO) group discovered a clever way around Google's security measures giving us full access to the rich data Google stores on the cloud for its users. Cellphone TrackingOur bulk cellphone location tracking program captures almost 5 billion records a day and feeds into a massive 27 terabyte database storing information about the locations of a hundred million devices. By tapping into the cables that connect the mobile networks globally and working with our corporate partners to install intercept equipment, we can apply mathematical techniques that enable our analysts to map cellphone owners' relationships by correlating their patterns of movement over time with thousands or millions of other phone users who cross their paths. This "Co-traveler" program allows us to look for unknown associates of known intelligence targets by tracking people whose movements intersect.Spying Toolbox: The ANT CatalogWhen the data we seek resides in places we cannot access using the above surveillance techniques, we rely on the technical experts in the Tailored Access Operations Group and their specialized tools from the ANT Product Catalog. The categories of available tools are listed below. Click on an icon above to view the related ANT products FBI Aviation Surveillance Operations (FBI Hawk Owl Project)An FBI fleet of over one hundred specially-modified Cessna planes equipped with sophisticated camera systems in steerable mounts that can provide detailed video, night vision, and infrared thermal imaging quietly fly circular routes daily around many major U.S. cities trackingtargets and gathering intelligence. Some of the planes use “augmented reality” software and sophisticated surveillance technology capable of tracking thousands of cellphones users.FBI Aerial Surveillance in the Continental U.S.Zoom in and click on the red map markers to view images of the unusual flight patterns in the FBI's targeted areas. View the map in full-screen mode.FBI Aerial Surveillance in HawaiiS. 1595: Protecting Individuals From Mass Aerial Surveillance Act of 2015In June 2015, a Senate bill was introduced to "protect" our citizens from Mass Aerial Surveillance. We are happy to report that no action has been taken on this bill and we have every confidence that Congress will agree with us that mass surveillance "IS" protection for our citizens. You can track the progress of this ill-advised bill below.Our Undersea Cable Tapping StrategyBy tapping into the worldwide network of undersea cables, our OAKSTAR, STORMBREW, BLARNEY and FAIRVIEW systems can process data as it flows across the internet. Each system is responsible for different types of intercepted data. For example, the BLARNEY system gathers metadata describing who is speaking to whom and through which networks and devices.There are two methods employed for tapping into the undersea cable network. A modified nuclear submarine houses the technicians and gear needed to place the physical taps on the undersea cables along strategic points in the network. The second method involves using intercept probes at the point where the cables connect to the landing stations in various countries. These probes capture and copy the data as it flows onward. 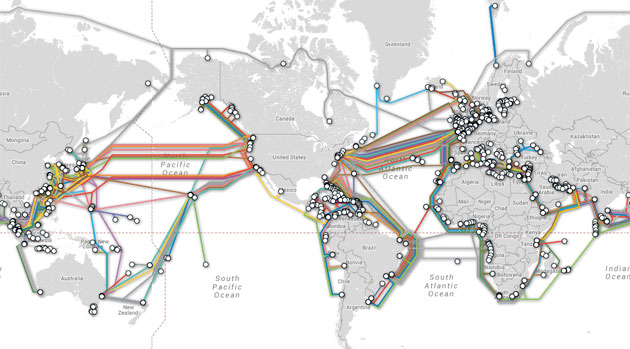 View an interactive map of worldwide undersea cables View an interactive map of worldwide undersea cables  This map illustrates our worldwide data collection access points This map illustrates our worldwide data collection access pointsXKeyscore: Our Real-Time Internet Monitoring CapabilityAs data flows through our worldwide data collection points, the XKeyscore system indexes and stores this information in a rolling three-day buffer database containing all internet activity passing through each collection site. XKeyscore is a massive distributed Linux cluster with over 700 servers distributed around the world.The theory behind XKeyscore is simple: People spend a large amount of time on the web performing actions that are anonymous. We can use this traffic to detect anomalies which can lead us to intelligence by itself, or provide a selection path for further inquiries. Examples of anomalous events: Someone searching the web for "suspicious stuff" or someone who is using encryption. This slide shows a worldwide map of the XKeyscore server locations This slide shows how metadata is extracted and stored in the XKeyscore database Learn more about the XKeyscore system. Tracking Our Surveillance Data: Boundless InformantThe "Boundless Informant" mapping tool provides our analysts the means to track intelligence collection statistics worldwide. Using a color-coded map, we can quickly determine the volume of collection data we have by geographical location. This global heat map assigns each nation a color code based on its surveillance intensity ranging from green (least subjected to surveillance) through yellow and orange to red (most surveillance). With the monthly domestic intelligence collection volume at almost three billion pieces, the United States is assigned the color orange. Learn more about the Boundless Informant program Surveillance Data from Other SourcesIn addition to our own data collection activities, the Domestic Surveillance Directorate receives a constant flow of information from other sources. For more information about these sources, see Our Partners below | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
++++++++++++++++++++++++++++++++++++++++++++++++Our PartnersDomestic Surveillance is a team sport. Our success depends upon our partnership with other federal, state, and local agencies. The USA PATRIOT Act was passed in 2001 for the purpose of "Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism". This far-reaching law gave us a wide range of new tools to detect and prevent terrorism. Our partners transmit a steady flow of intelligence information 24-hours a day from across the nation. The incoming data is indexed, stored, and shared throughout the Intelligence Community on our massive cloud computing network. Suspicious Activity Reporting - Fusion CentersThe Nationwide Suspicious Activity Reporting (SAR) Initiative (NSI) is a collaborative effort led by the U.S. Department of Justice in partnership with the Department of Homeland Security, the FBI, and state and local law enforcement partners. This initiative establishes a national capacity for gathering, documenting, processing, analyzing, and sharing SAR information gathered by fusion centers across the county. Located in states and major urban areas, fusion centers are uniquely situated to empower front-line law enforcement, public safety, fire service, emergency response, public health, and private sector security personnel to gather and share domestic threat-related information. Fusion Centers Location Map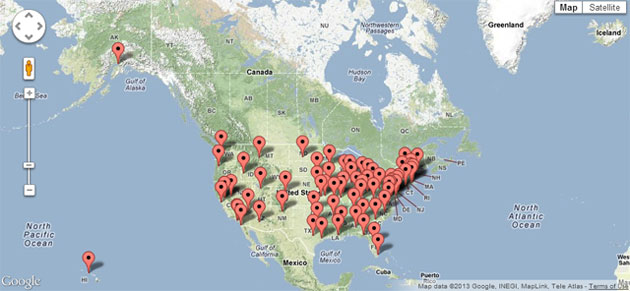 Click on map to locate your local fusion center Click on map to locate your local fusion center Suspicious Activity Reporting (SAR) Information Flow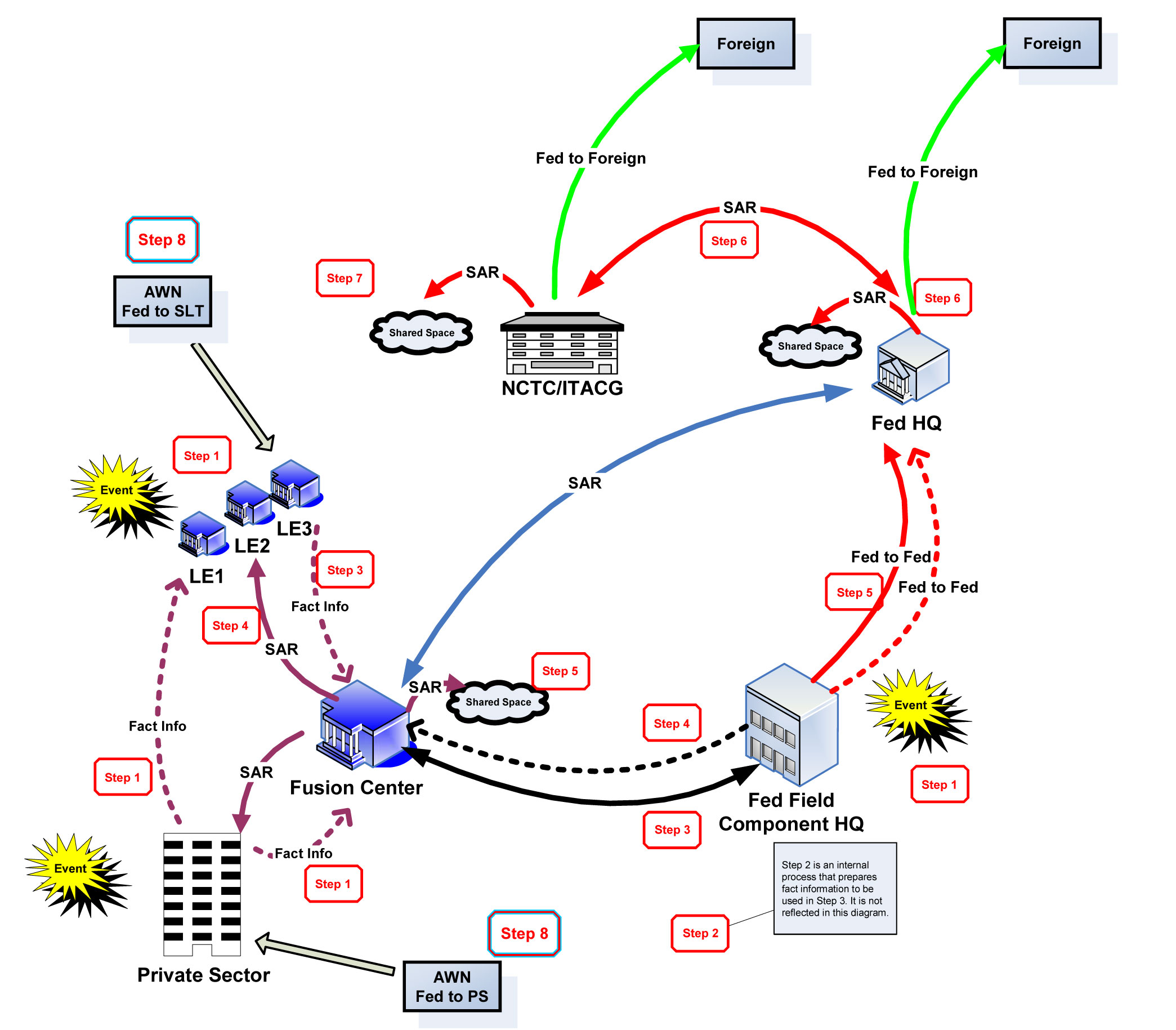 National Counterterrorism CenterThe National Counterterrorism Center (NCTC) operates as a partnership of more than 16 organizations including the CIA, FBI, State Department, Defense Department, Homeland Security; and other agencies that provide unique expertise such as the Departments of Energy, Treasury, Agriculture, Transportation, and Health and Human Services. The NCTC is the primary organization for analyzing and integrating all foreign and domestic terrorism-related intelligence possessed or acquired by the United States. It was also recently given the authority to examine the government files of U.S. citizens for possible criminal behavior, even if there is no reason to suspect them. FBI Terrorist Screening CenterThe FBI Terrorist Screening Center (TSC) was established in 2003 by Homeland Security Presidential Directive 6 which directed that a center be established to consolidate the government's approach to terrorism screening. The TSC maintains the U.S. government's consolidated Terrorist Watch list, a single database of identifying information about those known or reasonably suspected of being involved in terrorist activity. 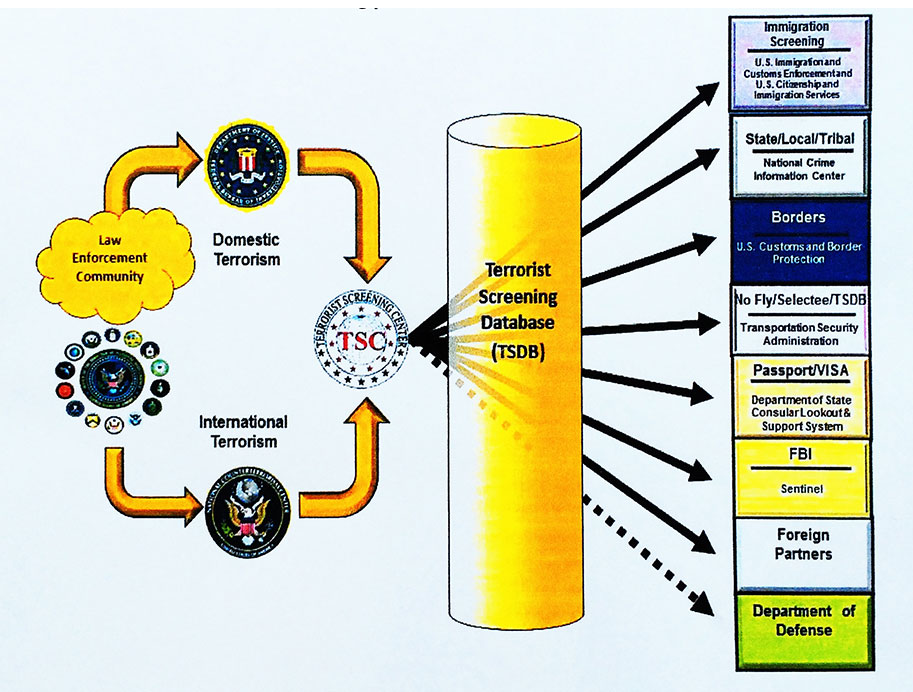 FBI Surveillance AircraftFBI airplanes equipped with high-tech cameras and sophisticated surveillance technology capable of tracking thousands of cellphones below fly circular routes daily around many major U.S. cities trackingtargets and gathering intelligence. The clickable map below shows the unusual flight patterns in some of the targeted areas. View full size map.Other Partnerships We Can Publicly DiscloseFBI - The FBI is our go-to partner for much of our nation's domestic surveillance needs:
CIA - The Central Intelligence Agency has publicly committed to increasing its data collection efforts. CIA Chief Technology Officer Gus Hunt explains why: "The value of any piece of information is only known when you can connect it with something else that arrives at a future point in time. Since you can't connect dots you don't have, we fundamentally try to collect everything and hang on to it forever." DHS - TSA airline passenger data; surveillance data from unmanned domestic Predator B drones patrolling the northern and southern borders Treasury - Cash Transaction Reporting and Suspicious Activity Reporting data U.S. Postal Service - The exterior of every piece of paper mail processed in the United States is photographed and stored by the "Mail Isolation Control and Tracking program". Some post offices have installed hidden cameras outside to capture and record the license plates and facial features of customers leaving the parking lots. United States Congress - In 2011, Congress extended three key provisions of the PATRIOT Act for another four years. (Senate vote / House vote). In 2012, Congress reauthorized the FISA Amendments Act. (Senate vote / House vote). In 2015, both houses of Congress passed the USA Freedom Act which legally codifies our dragnet data collection while happily appeasing the civil liberties folks (a double win!). State/Local government - Electronic transit cards; electronic toll collectors; vehicle information and location data captured by license plate readers; public transportation video/audio surveillance systems British Spy Agency GCHQ - The GCHQ (UK Government Communications Headquarters) through its "Mastering the Internet" and "Global Telecoms Exploitation" programs uses secret agreements with commercial companies allowing them to tap into the transatlantic fiber-optic cables carrying the world's phone calls and internet traffic. The GCHQ processes, stores, and shares this information with the NSA via the Tempora program. Yahoo - Secretly searches all of its customers' incoming emails for specific character strings provided by the NSA/FBI.  |



















Comments
Post a Comment